
How will the cybersecurity landscape change in 2017? Many businesses still feel woefully behind in their response to the pervasive threat of cybercrime. Let’s review how companies in different countries and different industries are rating their own cybersecurity strategies heading into 2017.
Cybersecurity Report Card – Barely a Passing Grade
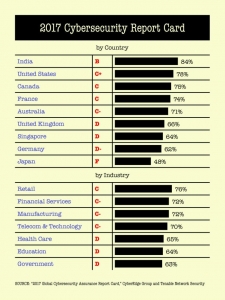
Researchers asked 700 security executives in nine countries how well their organization was dealing with cybersecurity threats including their assessment of the risk and their ability to reduce the risks given their security infrastructure. The average grade was a C-, with the US grading itself a C+. The “grades” in industry sectors were even lower. Regulated industries such as financial services and healthcare, rated themselves a C- and D, respectively. This may be the case not only because companies in these industries face substantial penalties for non-compliance, but also because hackers prefer to target these companies for their lucrative customer data.
China’s Censorship as Cybersecurity
In November, China announced that it will require US companies operating in China to disclose their source code as part of a security review process. China claims that they need to examine the source code to ensure that the software is safe from hackers. (Remember that NSA whistleblower Edward Snowden revealed to the public that the United States has been hacking Chinese government entities, businesses, and individuals since 2009.) Given that source code for most software products is proprietary and highly valued as critical intellectual property, US companies, including Microsoft, Intel and IBM are pushing back against this new regulation. The law is supposed to go into effect in the summer of 2017.
US: Bug Bounty Programs
Apple, Facebook, Uber and other large tech companies already pay bounties to “white-hat hackers” who identify security flaws in their systems. These hackers sometimes come over from the dark side to fight on the side of the software makers and ultimately their user bases. Apple offers up to $200,000 to hackers who find a serious security flaw. Nintendo offers up to $20,000 to hackers who report security vulnerabilities in their 3DS family of consoles. And yes, even the U.S. Army is trying this approach with Hack the Army Bug Bounty, held earlier this month.
What about other branches of the U.S. government and corporate leadership? Each should be more aggressive about pre-empting future cyber-attacks by identifying and fixing software bugs and network vulnerabilities either internally or externally.
It’s unclear how US President-elect Donald Trump will address the continual rise in cybersecurity threats. Will the new administration increase funding for U.S. Cyber Command, a branch of the US government that centralizes cybersecurity resources and operations? Will the new administration side with the FBI or with Apple if another dispute like the one over the San Bernardino shooter’s iPhone occurs? Will the government throw significant resources into defending against cyber espionage (and perhaps political sabotage) from state level actors such as Russia and China?
How can the average professional protect themselves?
Business professionals will still be at a great disadvantage in 2017 when battling against cybercrime, as new threats are continually emerging, and effective commercial solutions often take time to go to market. That said, there are basic measures every business professional can take to protect themselves from the most common forms of cyberattacks.
Using secure email communications, by sending encrypted email with RMail for example, is among the most basic and essential ways to protect your private or sensitive information. Additionally, be extra vigilant when you download apps, click on links (in email), and provide financial or personal information on websites; malware, phishing, and man-in-the-middle attacks continue to be pervasive threats to businesses and individuals.
Also know about Vishing & Smishing.
Wherever 2017 takes you, we wish you a happy, healthy, and safe New Year.
July 18, 2025
July 11, 2025

July 04, 2025

June 27, 2025

June 18, 2025