Pig Latin, Russian Spies and Email Encryption With the recent media focus on cybersecurity, whether it is talk of Russian hackers scheming to influence US presidential elections, or the pervasive pressure to comply with GDPR or HIPAA (healthcare privacy regulations) or other consumer data privacy requirements, “encryption” is one of the solutions that is often […]
Folklore of Opportunistic Privacy There is a wide body of people that believe they are sending information private because they are sending using Microsoft Office 365, Gmail, or using a third-party service that sends all messages using transmission layer security.
Your Friends Siri and Alexa Have Changed IT Security Your close friends Siri and Alexa may have done more to change how IT staff are re-inventing how they think about Internet security than years of tech tips and training sessions.
Is FOMO Today’s Addiction? LOL, LMAO, BRB, IMHO, OMG, BTW, FWIW, ILY, THX, JK. Ahhh, all of those elegant overused texting abbreviations that we all know. What about FOMO?
Do Recommendation Engines Make Us Simpler Minded? Recommendation engines operate behind the scenes everywhere, to make life a little more enjoyable, simpler, and more relevant. But do these make us all narrower minded?
Equifax’s $10 Billion Bet. You Really Don’t Care (Enough to Do Something) With so many big-name data breaches in recent times, your eyes may have glossed over the recent Equifax consumer data breach settlement. The numbers were big, 147 million consumers had their sensitive information exposed. The penalty, $700 million (or about $5 per person). […]
End of Summer Phishing, Hooks Office 365 Users The phishermen are getting smarter, using better lures to catch ever smarter phish (in this case, you, as an Office 365, OneDrive, SharePoint, or Dropbox user).
Now ‘TIS The Season for Security Autumnation Autumn May Bring Digital Serenity with Security Autumnation. Over the last year, while the user experience for technology has been progressively becoming simpler, the jobs of the business owner, IT director, and privacy and compliance officers have been progressively becoming more complex. Far more complex.
Beware of Hollywood Sim Swappers, The New Posers Hollywood Sim Swappers are the New Posers. Your mobile phone is often the second key to your life. When you forget your password at key accounts like your email or bank, you may be prompted to enter a code that appears by text message to your phone. […]
The Art of The Possible – Legislating in An Apple and Amazon World Apple, Google and Amazon have adapted extremely complex technology to the consumer world; and have forever changed the perception of what is possible with technology.

January 16, 2026
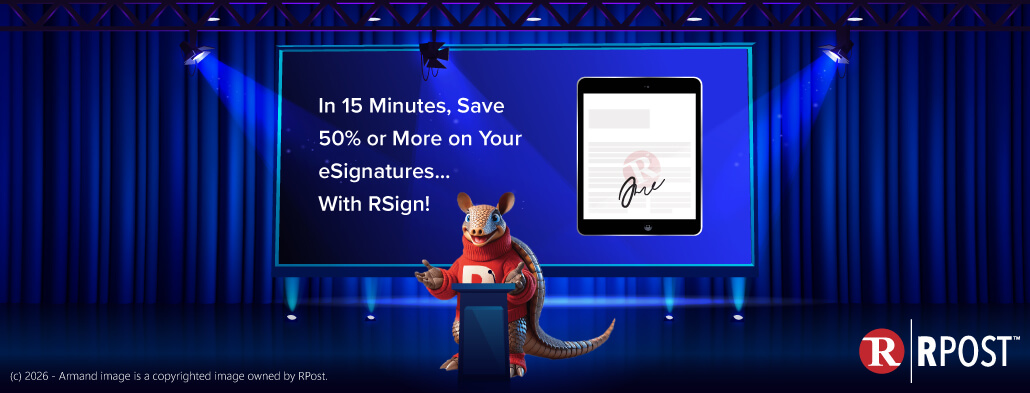
January 09, 2026

January 05, 2026

December 26, 2025
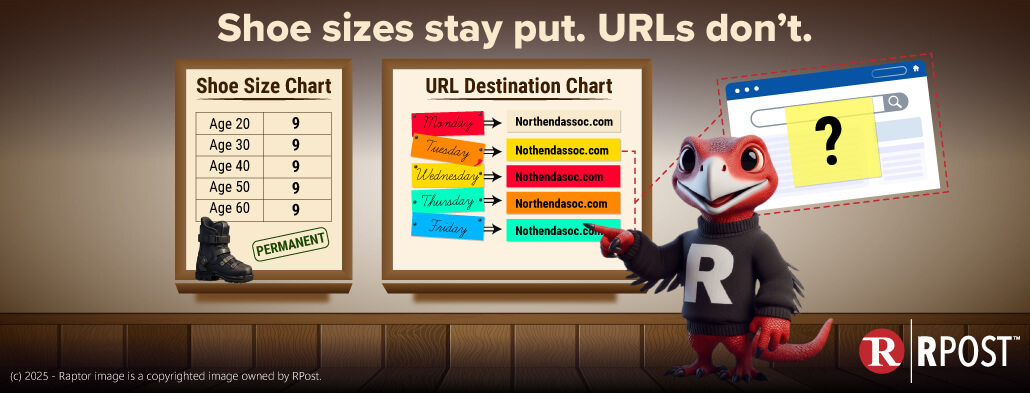
December 19, 2025