Armand here, RPost’s armadillo product evangelist. I don’t know about you, but I loved chemistry class. Learning about all those wonderful Elements and their combinations. For example, seeing what happens when you hold some magnesium strips over a Bunsen burner… What a wonderful chart of Elements, depicting the complexity of chemistry and the multitudes of possibilities combining some or more.
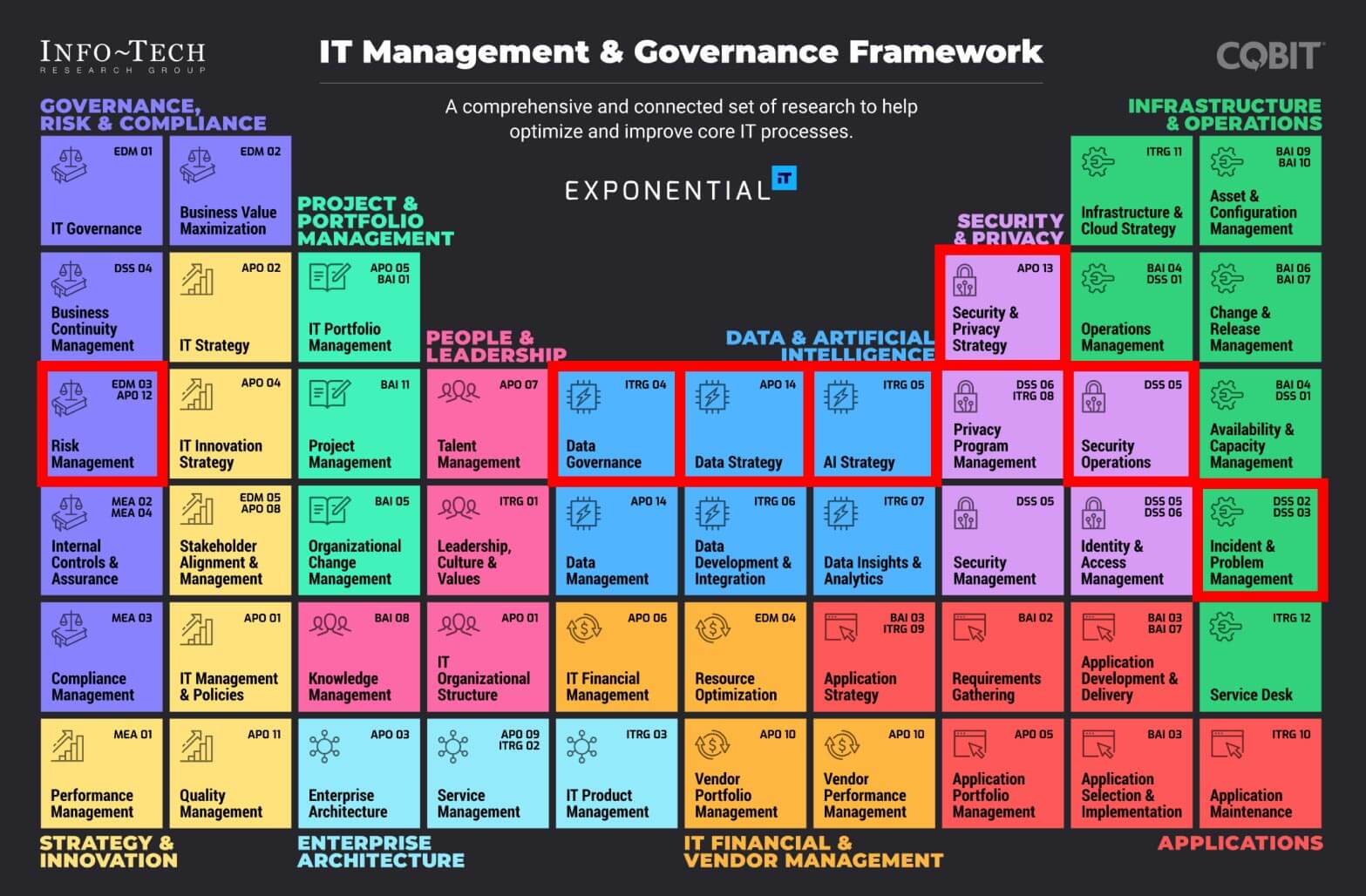
Back to information technology. I was taken aback recently when looking at the periodic table-esque chart of the functions a modern enterprise CIO needs to consider daily. This analyst view of the IT Management and Governance Framework reminded me of the Chemistry Periodic Table of Elements.
The challenge for CIOs today (one of many challenges) is that deploying advanced technology, for example to counter advanced threats, requires a cross functional view.
Let’s look at which functions deploying RPost’s Eavesdropping™ AI hits within this periodic table of CIO organizational function. Within RPost’s counter-insider threat and leak hub sits this core Eavesdropping™ AI that can detect when a cybercriminal or threat actor is actively eavesdropping on communications, transactions, or documents (a) in a compromised email account internal or at a third-party, (b) being sent to an impersonator receiving replies to lookalike domain email, (c) being sent from an insider that has either accidentally or maliciously leaked sensitive information.
Adapted from the original image. See source.
Step 1: First, one must evaluate the risk that this technology aims to thwart (Dark Purple: Risk Management). This risk mitigated is identifying early on if sensitive information is leaked to cybercriminals who then use the context of the eavesdropped-on information to power-up sophisticated cybercriminal financial and ransom lures. High risk? Yes! Check that box.
Step 2: Well, this seems to be associated with content data security. And, it involves use of AI within the tech to counter cybercriminal user of AI to steal. So then, off to the Data Governance, Data Strategy, and AI Strategy groups to evaluate (Green). Ok, yes, data protection is key and if good guy AI can counter evil empire AI, it seems strategic! Check that box.
Step 3: Ok now, off to the security and privacy teams (Light Purple). Surely, we must already have this need/tech covered, after all, we have a ton of network and email security detection, alert, and anomaly identifying components. Covered? NO!
It takes a keen eye to look at the tech with the ability to differentiate. This RPost tech can see the unseen today – it can identify the cybercriminal eavesdropping of company information OUTSIDE of the company network, for example, at third parties that one is legitimately doing business with, when/if they have a compromised email account or device. This is far different than the INBOUND email security filters, IN OUR NETWORK device anomaly detectors, and other internal monitoring tools that we have. Do we need this? YES! We need every unique tool and layer we can add. Check that box.
Step 4: Now we need to purchase this and manage the technology asset (Red) and then…
Step 5: Enable it within our operations (Green) and further, create processes to monitor alerts (Green).
So, there you have it. What seemingly is a simple decision to deploy sophisticated security in an enterprise requires dexterity to navigate the various functions that might need to weigh in at different stages of the need - identification, evaluation, strategic prioritization, application management, operational deployment, and event/activity monitoring.
Join our Jan 23 webinar on Insider Threats, Leaks & Third-Party Risks.
Is it worth it? Absolutely YES. Why? Cybercriminals today aim for total business disruption with their attacks. One incident can cost millions, or even billions in financial and operational value lost.
Go ahead, put RPost’s Eavesdropping AI into your process, or just trust us and bypass the process and deploy fast --- you’ll see results within days, when you see where cybercriminals are lurking with YOUR data outside of your networks and current visibility. Here's an example of a customer using this tool to identify an impersonation attack in progress.

February 27, 2026

February 20, 2026
.jpg)
February 13, 2026

February 06, 2026

January 30, 2026