 RAPTOR AI Uniquely Can See How Content Leaks at Third Parties Outside Endpoints, and Agentically Un-Leak Leaks.
RAPTOR AI Uniquely Can See How Content Leaks at Third Parties Outside Endpoints, and Agentically Un-Leak Leaks.
August 7, 2025 – Los Angeles, CA
RPost, a global leader in intelligent content security, today announced show casing its new and groundbreaking RAPTOR™ AI Cybersecurity Command Center, unveiled in tandem with the Black Hat and International Legal Technology Association (ILTA) security AI conferences in Las Vegas and Washington, D.C.
RAPTOR AI powers RPost’s PRE-Crime™ preemptive cybersecurity solution, providing users the ability to see which senders, recipients, third party information receivers, and content is naïvely or maliciously leaking. If unseen, threat actors will use the leaked information to inform them of context about who is communicating with whom about what when.
Gartner Research recently named RPost a Visionary for its PRE-Crime preemptive cybersecurity and Aragon Research recently named RPost a worldwide Leader in Intelligent Enterprise Content Management.
From within the RAPTOR Security Command Center, oganizations can detect cybercriminals staging their attack through AI-powered email and document risk analysis outside one’s network. RAPTOR can:
“Leaked content, if not automatically AI un-leaked by RAPTOR™ AI or our Double DLP™ AI, at best provides context to cybercriminals who use it to juice-up hyper targeted hyper contextual phishing lures sure to trick,” declares RPost CEO Zafar Khan. “At worst, these leaks can divulge sensitive state or corporate secrets that can cost much more.”
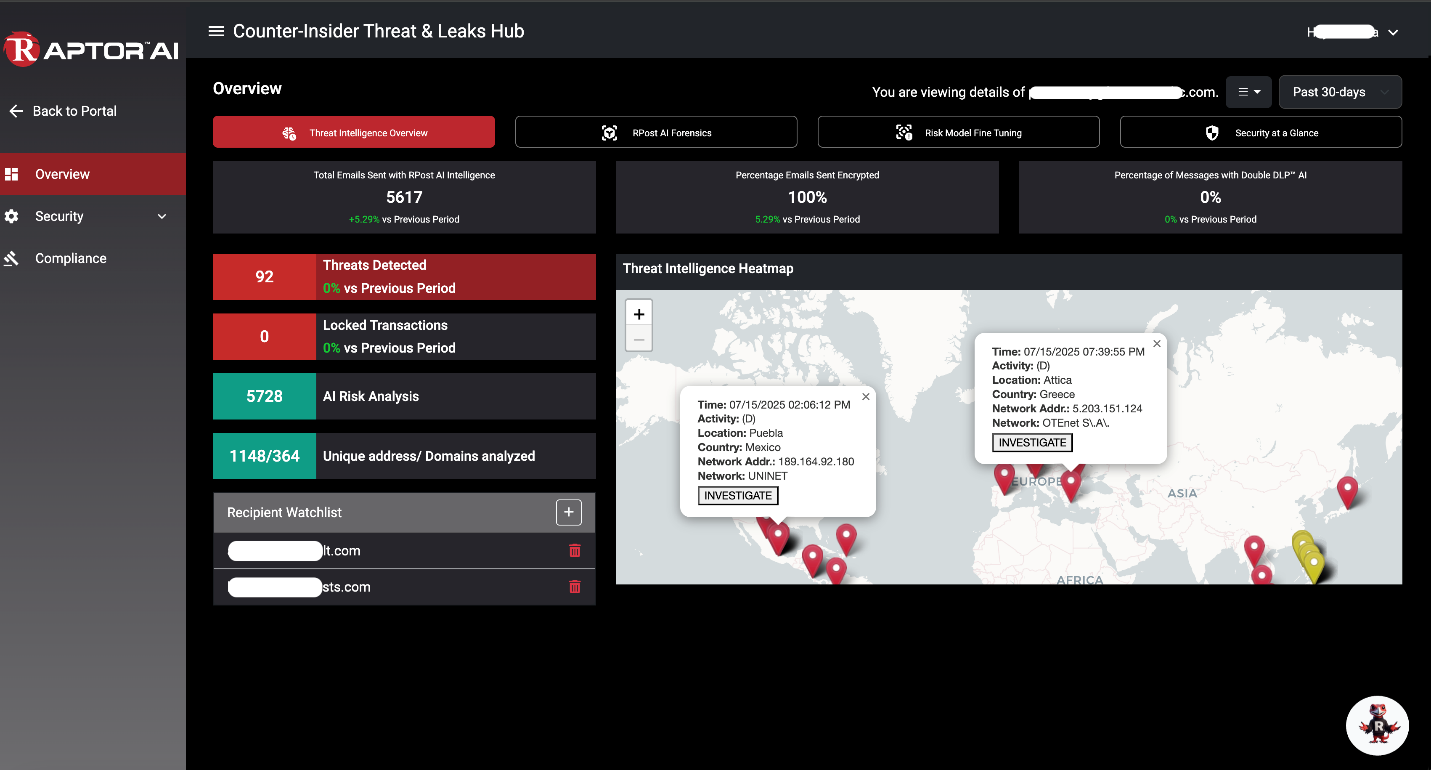
RAPTOR™ AI Cyber Command Center is centered on risk visualization and agentic actions within three dashboards: Real-Time Threat Intelligence Leak, Third Party Risk & Leak, and Double DLP™ Insider Threat & Un-Leak hubs. (See this video)
Admin View of One Sender’s Activity: Risk by ALL Recipient Messages with Yellow or Red Risk
Traditional DLP (Data Leak Prevention) gateways provide an outer perimeter for an organization to make decisions based on message or document content or other criteria. The software decision is typically, content permitted to send and thus permit the send, or content not permitted to send and thus block the send.
However, there are many situations where the traditional DLP filter needs to permit the send of sensitive information for the purpose of normal business operations. But what if the sender is tricked into sending to an email address that looks like the intended one but is trickily one character off; or perhaps the sender is sending to a Gmail address and mistypes one character. Or further, perhaps the recipient address is correct yet there is a cybercriminal or corporate espionage agent looking at the recipient (compromised) email account content?
There are situations where one is better served with an AI service that will identify all these things (and more) and pre-emptively trap the message out in the ether on route to the impersonated or unintended or intended compromised recipient. Double DLP™ AI operates in the ether outside of one’s endpoint perimeter and makes decisions to “delivery pause” or “auto-lock” content to preemptively un-leak otherwise sensitive content leaks.
Double DLP™ AI is an advanced cloud-based system that goes beyond traditional DLP by detecting misdirected or risky email transmissions and preemptively pausing or locking sensitive content to prevent data leaks.
RPost’s PRE-Crime preemptive cybersecurity solution and its RAPTOR™ AI Cyber Command Center are available worldwide and hook into a user’s outbound email flows. This AI security extends existing email perimeter security and neither requires software installation at the customer (user) nor at any third party.
About RPost:
We’re the global leader in premium, feature-rich and more affordable eSignature and cybersecurity services, and we’ve been continuously innovating for our customers the world over since 2000. From within our three main platforms: RMail email security and compliance, RSign eSignatures and RDocs™ document security and intelligence, we’re everything our customers need when it comes to email, document and form security, compliance, and workplace acceleration - track, prove, eSign, encrypt, share, certify, control, cure. We do what no other company does - all in one.
We thrive on ensuring that we are artisans and experts in everything we do: secure and certified email encryption for privacy and compliance; eSignatures and web forms to ease digitization of workflows; eDelivery tracking to prove important communications; managed file transfer to simplify secure sharing of large documents and sets of files; document-level digital rights management to empower control of document access even after transmission; and AI-infused apps to prevent data leaks by minimizing human eSecurity errors and locking out cybercriminal from exposed content. This is why more than 25 million users have enjoyed our RMail, RSign and RDocs™ services for over two decades across 193 countries. Learn more at the RPost website.

February 19, 2026

February 12, 2026

February 06, 2026

January 16, 2026

December 10, 2025