 PRE-Crime Preemptive Cybersecurity Powered by RAPTOR AI Called Visionary.
PRE-Crime Preemptive Cybersecurity Powered by RAPTOR AI Called Visionary.
July 17, 2025 – Los Angeles, CA
RPost, a leading provider of intelligent content security solutions, today announced it has enhanced its PRE-Crime™ preemptive cybersecurity solution with more capabilities to remotely kill leaks and to attribute leaks to leakers, content, and cybercriminal cabals. These modules are powered by RPost’s RAPTOR™ AI that uses custom AI models and agents--including natural language processing (NLP), large language models (LLM) and machine learning (ML) --to pre-empt leaks and identify leakers and leaks-in-progress.
“We’re continuing to evolve our AI infused cybersecurity to meet the sophisticated use cases and security challenges that our enterprise customers are asking us to solve,” remarks RPost CEO Zafar Khan. “Email, document or other data-level leaks, unfettered, can provide insights to cybercriminals in their reconnaissance phase to juice-up hyper-contextual AI powered lures that all too often lead to business disruption, data exfiltration, corporate espionage, financial crimes, or worse. PRE-Crime can kill these leaks remotely and then attribute the leak to leakers, and identify the endgame of the threat actor to preempt risk.”
Gartner Research recently named RPost a “Visionary” for its PRE-Crime preemptive cybersecurity solution, and Aragon Research positioned RPost in the “Leader” section of “The Aragon Research Globe™ for Intelligent Enterprise Content Management (iECM), 2025”.
Newly released PRE-Crime enhancements:
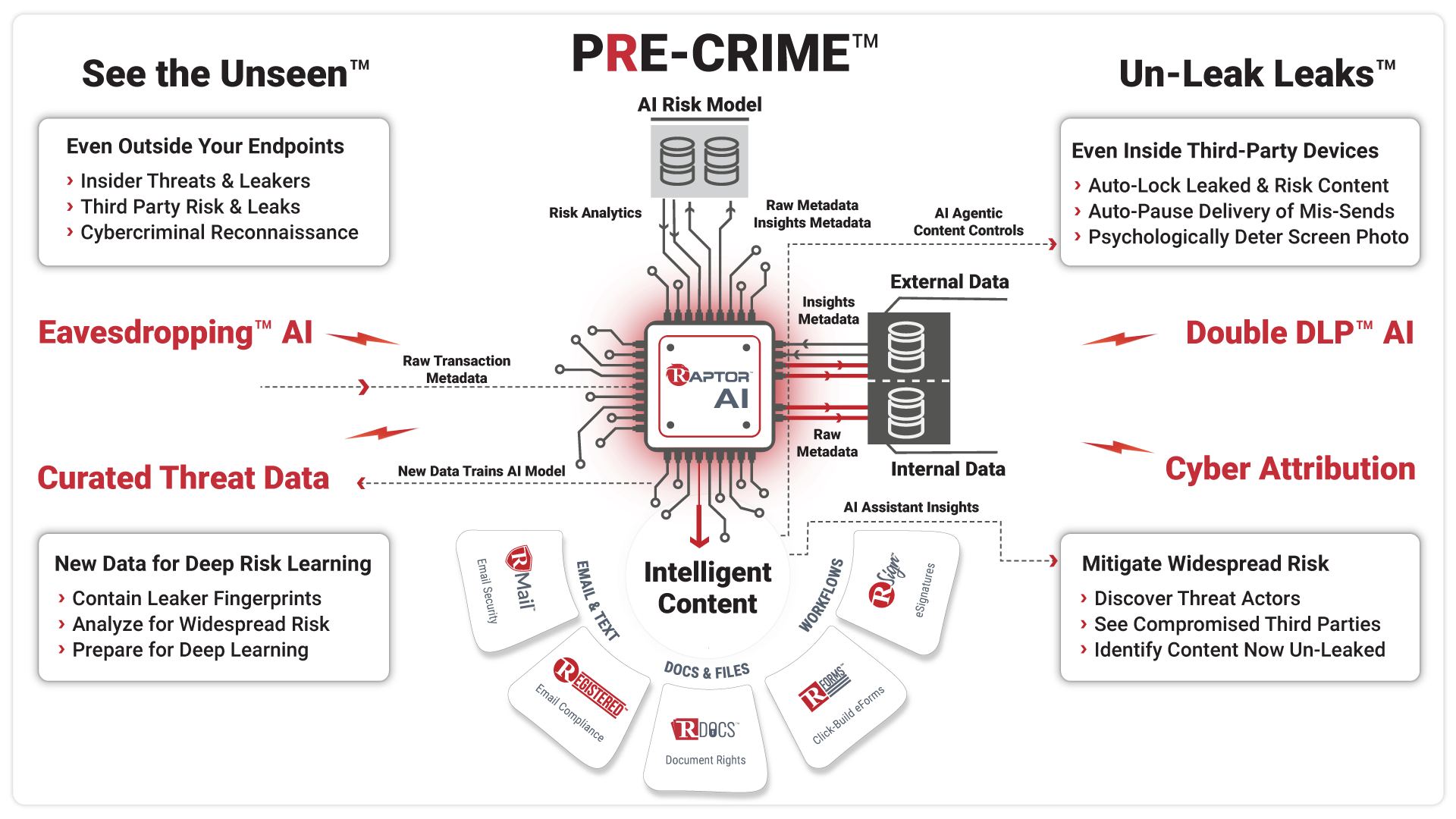
The Five Phases of PRE-Crime™ Preemptive Cybersecurity
RAPTOR™ AI: See the Unseen™
DOUBLE DLP™ AI: Un-Leak Leaks™
PRE-Crime is additive to existing systems with common hook-ins to enterprise infrastructure:
Top level use cases of PRE-Crime preemptive cybersecurity include:
Unlike traditional defensive reactive cybersecurity and traditional data leak prevention and document retention tools, PRE-Crime provides offensive cybersecurity, identifying, deterring and neutralizing threats before they escalate negating risk and remediation costs.
About RPost:
We’re the global leader in premium, feature-rich and more affordable eSignature and cybersecurity services, and we’ve been continuously innovating for our customers the world over since 2000. From within our three main platforms: RMail email security and compliance, RSign eSignatures and RDocs™ document security and intelligence, we’re everything our customers need when it comes to email, document and form security, compliance, and workplace acceleration - track, prove, eSign, encrypt, share, certify, control, cure. We do what no other company does - all in one.
We thrive on ensuring that we are artisans and experts in everything we do: secure and certified email encryption for privacy and compliance; eSignatures and web forms to ease digitization of workflows; eDelivery tracking to prove important communications; managed file transfer to simplify secure sharing of large documents and sets of files; document-level digital rights management to empower control of document access even after transmission; and AI-infused apps to prevent data leaks by minimizing human eSecurity errors and locking out cybercriminal from exposed content. This is why more than 25 million users have enjoyed our RMail, RSign and RDocs™ services for over two decades across 193 countries. Learn more at the RPost website.

February 19, 2026

February 12, 2026

February 06, 2026

January 16, 2026

December 10, 2025